IS YOUR COMPANY AT RISK?
The Fastest, Easiest, and Most Affordable Way to Protect Your Business From Internal and External Threats.
Critical data loss can stop a business cold.
9 out of 10 computer networks have potentially serious IT problems sitting undetected.
We hate SPAM and promise to keep your email address safe.
or call us at 1-844-CYOLOGY
Identify Your Organization’s Security Deficiencies and Areas of Strengths and Weaknesses
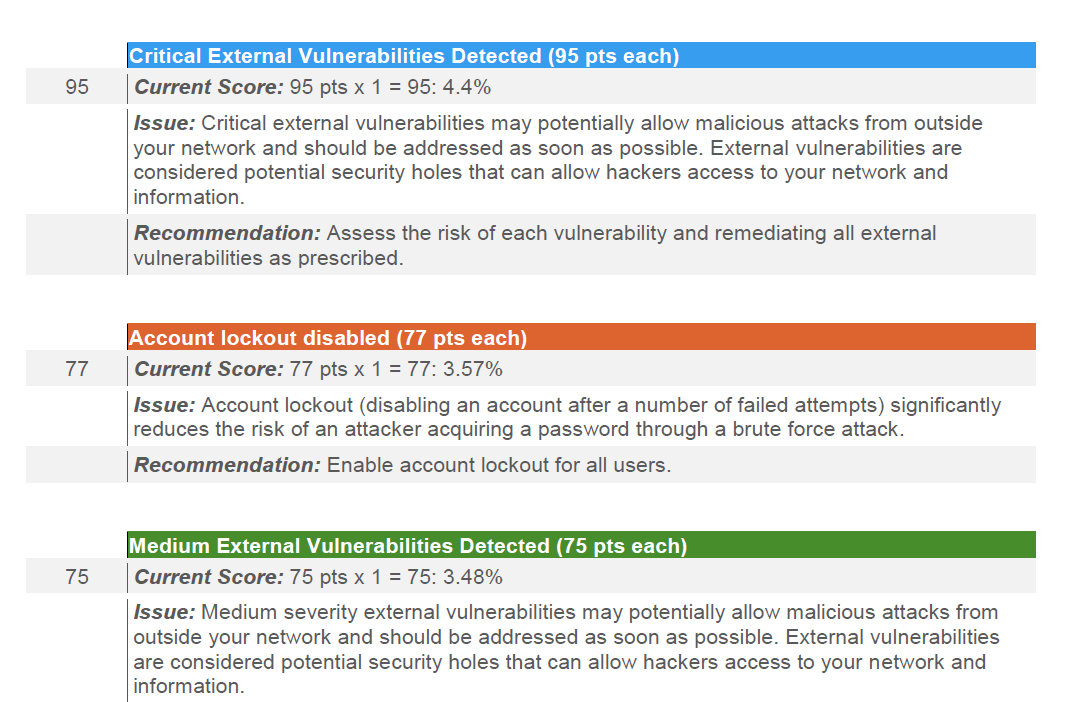
Review The Security Posture of Your Organization’s Network, Devices, and Applications
Cyology Labs’ report card audit is uniquely designed to improve understanding of the level of your organization’s security and also identify security deficiencies as well as areas of strengths and weaknesses. These will go a long way in helping you to:
- Correct security issues before leading to downtime.
- Identify problems that are causing slow performance, frequent virus attacks or communication problems.
- Develop an action-plan to correct dangers and reduce the associated risks.
Are You Planning To Expand Your IT Capabilities?
If you’re planning to expand your IT networks, you shouldn’t overlook proper management, performance optimization and security.
The network and security assessment report provided by Cyology Labs' report card audit will help you to pinpoint and correct any existing issues before you add new IT solutions. This will help to protect your business from increasingly sophisticated and widely available attacks while expanding your IT networks.
Protect Your Business Today! Choose Your Plan Below.
|
Computer Security Report Card |
The Computer Security Report Card assesses individual computers based on security criteria. Devices discovered on the network are assigned an overall score, as well as a specific score for each of the assessment categories detailed in the report card.
|
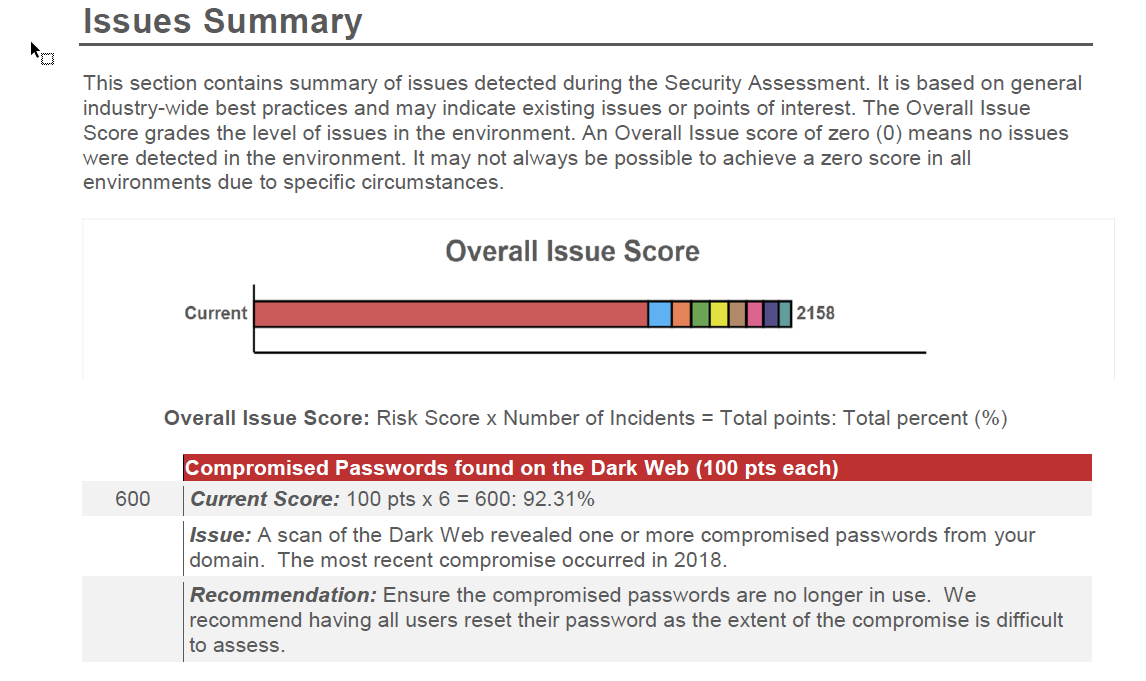
Security Risk Report |
The Security Risk report is your proprietary Risk Score and chart which shows the relative health of your network security, along with a summary of the number of computers with issues. This powerful report also details outbound protocols, system control protocols, user access controls, external vulnerabilities summary, and dark web password and credential breaches.
A Full Network Assessment Report to help you locate the specific findings of interest, and problem areas are conveniently highlighted in red, making it easy to spot individual problems to be rectified.
BONUS: Report providing guidance on which issues to address by priority |
-
Assess individual computers at a high level based on various security criteria
-
Assess Anti-virus / Anti-spyware
-
Assess Missing Critical Patches
-
Assess Insecure Listening Ports
-
Assess Failed Logins
-
Assess Network Vulnerabilities
-
Assess computers to ensure Screen Lock with Timeout policy
-
Report on Aging Systems
-
Detect and Report on Supported / Non-Supported Operating systems
-
Detect outbound protocols that should not be allowed.
-
Detect system controls for protocols that should be allowed but restricted.
-
Determine if controls are in place for user web browsing
-
Detect and determines if wireless networks are available and secured
-
Documents domain computer and domain controller security policies
-
Documents and assesses consistency of local security policies
-
Establish a Risk Score to determine significant risks and potential issues
-
Password complexity check
-
Automatic screen lock check
-
Scan for Compromised Passwords found on the Dark Web
-
Account lockout policy check
-
Content Filtering Check
-
Local Security Policy Check
-
FSMO (Flexible Single Master Operation) Role Analysis
-
Assess the users in AD, status, and last login/use, which helps identify potential security risks
-
Assess all major apps / versions and counts the number of installations
-
List the non-Active Directory devices responding to network requests
-
Listing of event log entries from the past 24 hours for the directory service, DNS
server and file replication service event logs -
A Full Network Assessment Report to help you locate the specific findings of
interest, and problem areas are conveniently highlighted in red, making it easy to
spot individual problems to be rectified. -
BONUS: Report providing guidance on which issues to address by priority
FAQ
Here are a list of questions we often get asked about before performing an audit.
I've purchased and scheduled my audit, what happens next?
You review and sign a document permitting Cyology Labs to audit your network. Then we'll setup a remote session into your computer and run our collection software. Once we receive the collected data, we can then produce a report for you. NO CORPORATE DATA WILL BE SENT TO CYOLOGY LABS
How long does the audit take to run?
The audit can run between 30 minutes and 5 hours depending on how many devices are in your network. The average is about 30-45 minutes. The best part about this audit is that there’s No software to install, and No endpoint agents to deploy. It’s painless. It just talks to your network devices via WMI to pull critical information from them so that we can run the report.
Will this report ensure I'll never be hacked ?
No audit will ever ensure that you won't be breached. As a business owner or IT administrator, it's your job to make sure all the "Door and windows" are secure on your network, but unfortunately there's no silver bullet to stop a hacker, the hackers just need 1 way in. This audit how ever will show you where to start to ensure the network is difficult enough so that the hackers move on.
I have a new Firewall installed, why do I need an audit?
While most businesses protect their systems and data against external threats like malware, many overlook the biggest cause of data breaches: internal risks. Internal vulnerabilities are responsible for 70% of all data breaches in small and medium sized businesses (SMBs). These audits will help you pinpoint these weaknesses and help you correct them before a Cyberattack causes an outage.
I trust my employees wholeheartedly, what would this audit do more for me ?
If you think most data breaches are due to malicious insiders, you’d be wrong. Forrester found that only 12% of security incidents are caused by disgruntled employees with mal intent. Whereas, a whopping 27% of security breaches were caused by employees’ inadvertent misuse of data.
This means that if your company does experience a security breach, it’s 2x as likely to be perpetrated by a reliable employee rather than disgruntled worker.
In short, your best employees could also be your greatest risk.
I already have an IT department and they tell me everything is fine, tell me why I need an audit from Cyology Labs ?
The only way to know if you are protecting your business is to know what is happening inside your network. If you or your IT department aren’t currently running regular reports, or your current service provider isn’t running a regular assessment, briefing you on that assessment, and updating your management plan, then something crucial might be getting missed.
A comprehensive Cybersecurity solution should include ongoing internal vulnerability detection, alerts, and remediation options.
Even if your company is able to effectively detect internal vulnerabilities, experts recommend hiring a third party to evaluate risks at least once per year. Not all security service providers are the same. We can provide and perform this important task for your company.
To learn more about how to prevent internal vulnerabilities, contact us today at
1-844-CYOLOGY.
.
CONNECT ON SOCIAL MEDIA
Don't Wait Until It's Too Late To Be Up To Date. Download Fraudster On Your Mobile

Contact Us at 1-844-CYOLOGY
© Copyright 2024 Cyology Labs & TerryCutler.com . All Rights Reseved.




